 NAPS2 - Scanner Sharing
NAPS2 - Scanner Sharing Scanner Sharing
Scanner SharingNAPS2 allows you to use scanners connected to one computer from any other computer on the local network. Scanners can be shared across Windows, Mac, and Linux using the ESCL driver.
On the computer the scanner is connected to, you can open the "Scanner Sharing" window from the "Profiles" window (or the "Scan" dropdown).
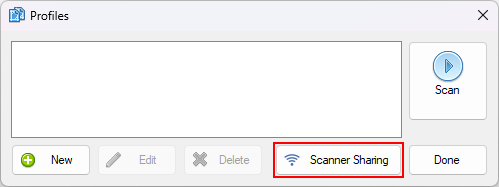
Click the "Share" button.
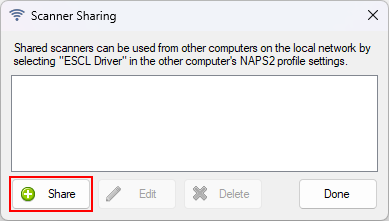
Select the scanning device that you want to share. You can also change the name that other computers will see.
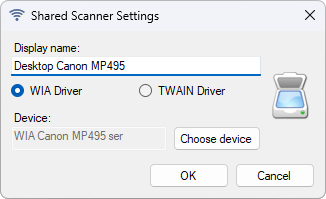
You can share as many devices as you like. They will be available as long as NAPS2 is running.
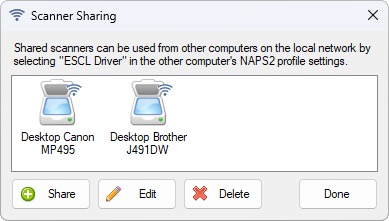
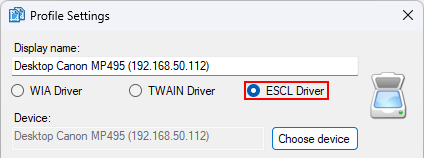
On the computer you want to scan from, create a NAPS2 profile with the "ESCL Driver" selected and choose the shared scanner.
Then you can scan!
Scanner sharing uses the standard ESCL protocol, which means it works with any ESCL-compatible client, including on Android or iPhone. Some examples:
If the server is running Linux, you don't need to use NAPS2 if you don't want to:
Or, if the client is using Windows and the server is using Linux, you can use SANE over the network if you install SANEWinDS (v1.2+) on Windows. This doesn't use ESCL - instead, SANEWinDS provides a TWAIN device on the client that will connect to the SANE server.
Scanner sharing currently only works while NAPS2 is running on the server. Running as a service is planned but not currently supported.
As an alternative to using automatic device discovery you can select the "Manual IP" option on the client.
For the port number, NAPS2 uses 9801-9850 for HTTP and 9901-9950 for HTTPS, in ascending order for each shared device (skipping any already-in-use ports). Ports are "sticky" so the port associated with a particular device when you first share it won't change.
ESCL uses mDNS for automatic device discovery, which involves both the client and server sending multicast packets to UDP 224.0.0.251:5353 (which get delivered to everything on the network).
If you have a network firewall, you'll want to make sure it allows both the mDNS packets and direct IP to IP connections between the client and server.
If you want to allow a limited port range, NAPS2 uses TCP ports 9801-9850 for HTTP and 9901-9950 for HTTPS.
NAPS2 always checks mDNS when scanning, meaning that connections should still work even if the server IP changes (as long as you're not using the "Manual IP" option).
If your client and server are on different subnets, mDNS packets usually aren't transferred across subnet boundaries so automatic device discovery won't work by default.
You can use Manual IP Connections in this case. Or, if you want to try to fix service discovery, there are some possible solutions:
By default, scanner sharing uses HTTPS with an auto-generated self-signed certificate, but may fall back to HTTP if there's a problem. Admins can force HTTPS to always be used or provide a custom certificate.
Back to Support